Custom Software development involves following the entire custom development lifecycle process so that the project in hand reaches its success. But, many fail to see the amount of hard work, worries and frowns that go behind the entire process. In recent times, with the onslaught of cyber attacks and security lags, only developing software is not enough. Developers and collaborators also encounter various issues including ensuring security at every step of the custom software development cycle. This is primarily the reason why pro-active managers ensure that this feature is covered at every stage of the cycle. They depend on in-house security specialists and also outsourcing partners in order to curb this issue.
Data Breach is a serious issue!
We are all aware that in 2019 March, Facebook admitted that it did not thoroughly secure the passwords endangering the security of 600 million users. Even giants like Microsoft have faced data breaches that allowed hackers to access email accounts through Microsoft customer support. One small blunder or a mishap in the custom software development cycle and the repercussions can be extremely harmful which will have a resounding effect on the entire process. Clouding the effects of the breach can be an expensive process and Statista estimated that it had cost $2 trillion to organizations to overcome and rectify the effects of Cyber Crime.
Software testing companies believe it is important to implement security issues at every stage of the cycle in order to guarantee the success of the software development lifecycle. Management also should ensure continuous engagement with stakeholders throughout the development process because it is important to uphold stakeholder’s expectations and also to reiterate that the good custom software development project should resonate great designing and should have great security features to complement the software.
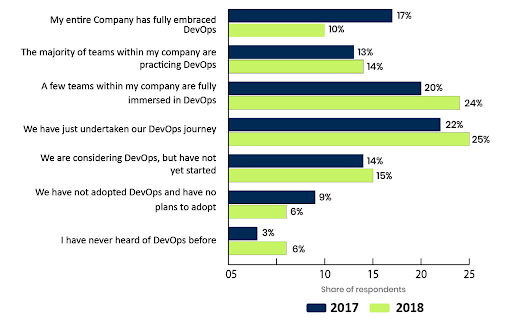
From the illustration itself, it is clear that businesses over the years have faced the wrath data breaches.
Traceability is the key
One thing that has to be enforced in the entire SDLC process is traceability implying that all the requirements of SDLC especially the security requirements should be traced in all the phases of the process to prevent roadblocks. Crystal clear objectives have to be set and with proper traceability, the chances that the client accepts the final product in one go becomes heightened.
Let us now explore how security measures can be laced in every stage of the custom software development process. But, first, we will understand the processes involved in the custom software development cycle.
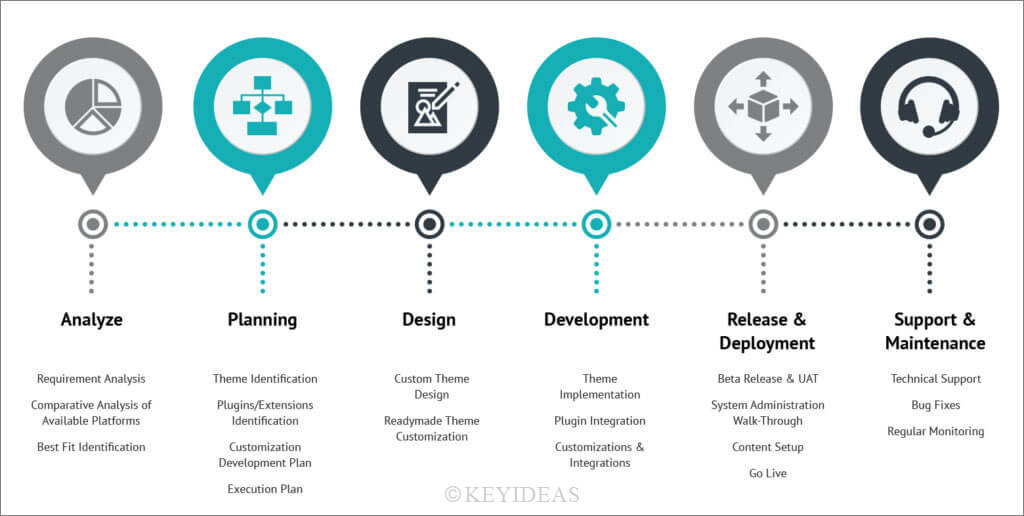
Source: Key ideas Infotech
Well, as is apparent from the above-given process flow, we see that it is a six thronged process. Out of these 6 key processes, Analyzing and planning have assumed greater importance mainly because it forms the basis of the remaining stages. Based on what is being planned and analyzed will the product turn out to be the way it has to be!
How to infuse features of security?
Get an idea about the outlook
At the beginning of the cycle, understand what the client actually wants. This can be done by asking relevant questions to the client related to;
- Building base and perimeters of the project
- Understanding the people involved in the project
- Guesstimating the process gaps
Once you get the holistic picture, software development companies should craft tailor-made security-centric processes that define the project scope and needs. This phase is important to analyze the requirements of the software. It will ask questions like
What will the software do? What are the resources needed to build the software and finally based upon understanding; What are the other resources that are needed to build it?
When you do this, a host of weaknesses will be exposed upfront in the early stages itself. Internal security experts or the ones the company is outsourcing can do a world of good by understanding these glitches and take preventive measures right at the beginning. They will then ensure that information security issues can be integrated into feasibility studies.
At the design stage too, security concerns should be addressed and not as a whole but in bits and parts. For instance, the database requirements, system flow diagrams and the security design should all have varied forms of security concerns that have been covered. In these stages, threat modeling also should be covered which has the knack to predict when the attack might occur and it gives a pre-hand in visualizing as to what could be the consequences of the threat. Every team stakeholder should consciously allot time to this process even if it eats into the development process time. Efforts in this stage will imply rewards later. So a custom software development company should consciously do this and should make the clients realize why it is an important step.
Security-focussed requirement gathering is key
In the nascent stages if software testing companies start by generating security requirements it will establish firm grounds for instilling a mindset that talks about security. Abuse and misuse cases should be generated and risk analysis should be carried out in the requirements gathering stage so that the process has a trickle-down effect on the other stages of the custom software development cycle. When this happens, focus on security will never be deviated.
Development is above all!
Most of the time that is been invested is during the development phase. It includes some of the most crucial operations that include coding and building the software. Code problems can be sensed and picked out with several tools like static and dynamic application security testing which aids companies to understand where the coding has faltered and what could be the probable security weaknesses. When issues are caught upon real-time then engineers can program them back to normalcy treating the problem at its roots.
To identify weaknesses in codes, a lot of time has to be invested after coding errors have been identified. The coding team at Chapter247 ensure that we follow all the guidelines for eliminating coding errors. Software development companies have to ensure that the same coding errors are not repeated else there is no point in discussing the errors and dwindling time.
We ensure that all the people involved in the custom software development cycle get their hands on the latest information and development practicing. Training prior to development is an essential process in the chain. It is important that when the development begins there are no clashes of interest and the scope of every custom software development project is clear.
Perform Secure code review
The main aim of performing a secure code review is to improve the quality of the code and also to upgrade the skill level of the developers so that they create optimum codes for the project. Developers have to accept their folly in coding at this stage which will only help them to create better codes.
Testing stage
We all know that for developers, testing is one of the most crucial processes because it is that one ground on which their software goes through the test of its time. Here they will be able to identify if their solutions have been good enough to save it from hackers before it is released to the market. Just clearing out bugs is not the only thing that should be done here, but security testing also is an important part of it all. This process is equally important which a few managers tend to neglect or overlook.
At Chapter247, Software testing is a crucial process wherein a team of experienced developers create the software and test it at every level. There is not just one stage of testing which is followed by a multi-layered stage of testing procedures with clients and experienced professionals. Let the highly-specialized programmers look for security loopholes during the testing phases and guide manual testers with automated programs to abridge the entire team of the situation. Internal security experts or the outsourced team or security agents will do a world of good to the testing process in the custom software development cycle. Remember testing and security are not two different things, they are rather one process embedded in the other and required at this stage.
Penetration testing
Since we are talking about the testing and verification stage, it is important to understand how the product performs in its run-time. Penetration testing will help companies to understand how well a product is able to manage the abuse cases like logic glitches, bypass pursuits despite clearly indicating authorization breaches and a questionable security posture.
For all those who are not clear about what a penetration test is, it is a simulated cyberattack aimed at checking system vulnerabilities and how it can be exploited. It is more like an announced sting operation on your software. For complicated web application security issues, penetration testing is used to enhance a web application firewall.
Create a Software Security Group
A software security group will go a long way in ensuring software security is deeply engraved into the SDLC. It is a great way to gauge, train, educate and apply noted security measures throughout the process. This will help the team to manage risks effectively. SSG will act as the facilitators for software security by conducting 3’rd party security evaluations in the most important stages of the custom software development cycle.
End it with Post-implementation security
Now with the different procedures, we have enumerated for you and when the approved software has reached the implementation stage, the monitoring of security and consolidation has to continue. The post-implementation stage implies it is ready to be launched for the public eye. Here the user-feedback is very important to see to it that software is functioning in the planned manner and that if further loopholes have been discovered by the end-users. For this to happen one can avail the services of software security analysts who evaluate software post its release as a public service to point out security flaws that might arise later.
Also, prepare the internal team to add more to the process if the need arises. A pre-hand incident response plan should be outlined to address issues when they become a reality.
A parting note
The best part about custom software development cycle is that it is defined in stages. The benefit of doing this in stages is that it helps identify security lags in every stage. These security checks can be integrated into all the processes which will give your software project a major boost.
Our team involved in the custom software development cycle ensures that all the due diligence is followed with respect to the custom software development. We believe in what IIA research foundation has explicitly implied;
“Information is a significant component of most organizations’ competitive strategy either by the direct collection, management, and interpretation of business information or the retention of information for day-to-day business processing. Some of the more obvious results of IS failures include reputational damage, placing the organization at a competitive disadvantage, and contractual noncompliance. These impacts should not be underestimated.”








