If you are planning a cloud migration anytime soon from on-premise data storage to cloud-based platforms then you have come to the right place.
We all are aware that at one point or the other cloud migration becomes necessary, but to do it securely can be a challenge. If that’s the case, you are not alone. Chapter247 has helped countless enterprises prepare to move legacy on-premises data in the cloud using deep insights ensuring data security.
Cloud Migration is the process of moving your data usually in the form of files, emails, and software applications from local IT infrastructure which is managed in-house to cloud storage which is managed for you by a vendor. There is a very good basic reason to migrate to the cloud because it reduces overhead expenses and increases flexibility to expand their storage requirements. There is no need to purchase and commission physical servers in a data center. We have also observed that many businesses choose a hybrid approach which means that some of the data stay within the organization’s on-premises while some move to the cloud – a decision left to individual enterprises based on security policy or data sensitivity.
You will also love to read our feature on which one to choose – on-premises or cloud to begin with!
Some strategy considerations
The best decision you can take is to avail the services of a cloud solutions provider to migrate data quickly and securely. Remember it can be nerve-racking to move data with little or no downtime and at the same ensuring that the data is migrated to the right location. Also, what needs to be kept in mind is that the data is accessible to the right people when it gets there. Taking this forward we are recommending some serious considerations you should give while planning a migration.
-How should sensitive data be rightly handled? There are many privacy regulations that need safeguards for identifiable information. Important and critical data like contracts or IP should be treated and dealt with extra care.
-Understanding which data should and should not be migrated is yet another key consideration. You need to figure out which data is obsolete so that you can save on storage costs and reduce the additional layers in your migration work.
-Post-migration there has to be a strategy in place as to which users can access data. Remember you can’t accidentally rule out people to access data especially when it is an important part of their jobs. As an efficient cloud solutions provider, we will ensure that you don’t accidentally open data access to just about anyone in your organization.
Hence cloud migration is the process of transferring data, and workloads over to the cloud infrastructure. It makes an organization independent which means that anywhere access has made migration in cloud computing among organizations of all sizes and scales. COVID-19 has also been a major catalyst for the process because Cisco reported that Cloud data centers will process 94% of workloads in 2021.
87% of the global IT decision-makers also believe that the pandemic has been a major catalyst for cloud embracing.
It is also important to note that the cloud has other interpretations. It can also be referred to as a process of moving back to on-premises from the cloud which is reverse cloud migration apart from the conventional. The cloud movement irrespective of the type requires sufficient planning and know-how of the process for secure and error-free execution.
Our Guidebook on how to do it well
Our guidebook will be a good reference point that will work for any migration. We hope that this serves as a strong foundation and guide for you all.
Understanding your data
Gaining full visibility of your on-premise data is a huge challenge. Migration projects are a serious one needing your time and energy along with the cloud solutions provider. Before going for this, you need to have a clear understanding of the nature of the data you hold meaning you have to have a well-documented framework of the size, sensitivity, and risk profile of the data. Once that is understood, you need to identify which data sets will come first.
Take a look at disparate information
The first step peters out the case of irrelevant information but what about the several unstructured information? The team of Cloud experts at Chapter247 helps you get a detailed preview of your unstructured data. To make it secure we work through a process that will help you answer questions like:
-Who has access to the data? Is the data in question sensitive and is easily available?
-For any user or group, you need to prime out what data they can access.
-The same users who are already having that access, the enterprise should know the answer to – How did they get the access, what are they doing with it, and do they need it further!
Passwords have to handled with utmost care
Needed but also the weakest link is the password factor. A recent survey conducted by MobileIron and IDG estimated that 90% of the security professionals in the survey have witnessed cases of attempts to illegally access data because the credentials were either stolen and shared among too many users. Unfortunately with cloud computing in the picture, the vulnerability has been further exploited with passwords. There is no doubt that with cloud services organizations are given multiple opportunities to streamline and control the way data is handled but the risk with stolen credentials is on the rise.
As a practice, it is always better to keep a tight regimen on questions of accessibility. Have more accountability when it comes to users accessing data and keep changing the credentials on a regular note to ensure that such practices are not repeated. A double-factor authentication also is a useful step in that direction.
Look at our detailed review of best security practices and essentials forAmazon Cloud
Determining data owners to sensitive data
As a cloud solutions provider our algos are good at figuring out who should and who shouldn’t have access to data. But best practice is to assign data owners to critical data sets. Then the data owners who have access can make critical decisions based on business context. We have both quantitative and qualitative methods to understand which data should have an owner and if yes who should the owner be.
Conduct entitlement reviews
Once the data owners have been established, a pre-migration entitlement review is a must to weed out excess access. It should be easy for the data owners to review and revoke access through the procedure. Once a month entitlement review will help you understand the dynamic changes which have become a part of the process now. Each department can have a separate review schedule. When the review is completed, the owner should be notified if the folder in question contains what kind of data and how to handle it.
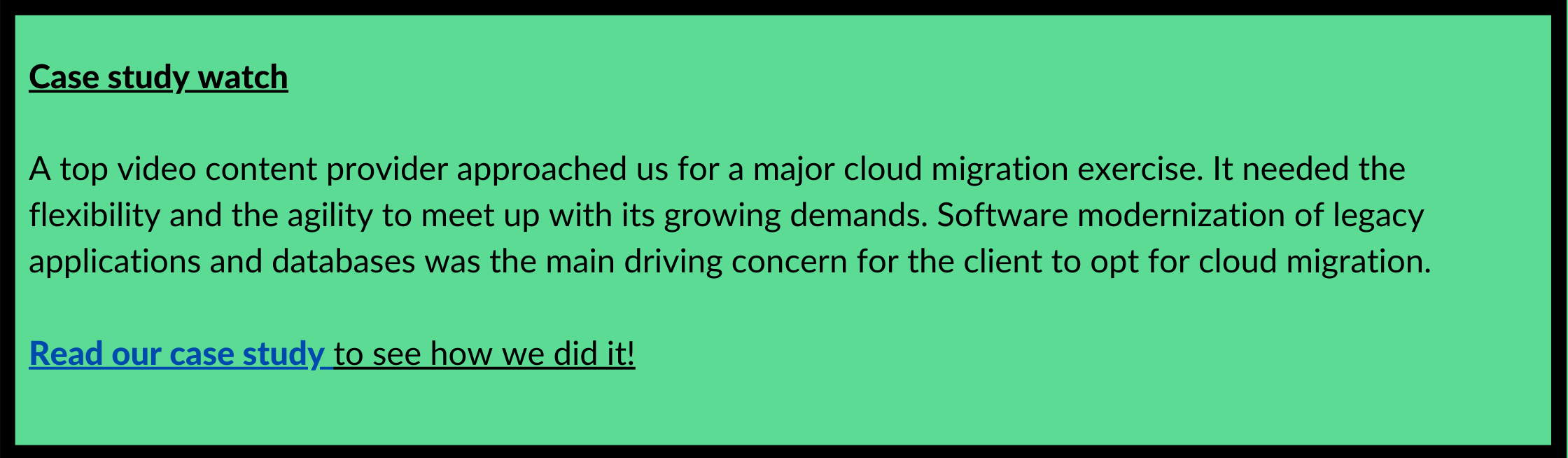 How Chapter247 Helps you in the process
How Chapter247 Helps you in the process
We ensure that the process of migration is done from a multi-hand perspective. Hence we evaluate existing assets and architecture of the current application and optimize the contribution in a manner that will align well with the overall business goals.
Interested in understanding secure cloud migration practices? Let our experts guide you!







